The configuration options available in Azure Active Directory Conditional Access Policies have grown rapidly over the last few years, and not implementing them at this point would not only be a waste of available features, but more importantly not provide optimal security configuration for cloud resources. Over the last few years of implementing these policiesContinue reading “Azure AD Conditional Access Policy Templates”
Author Archives: 365Pete
Defender for Endpoint
What is Microsoft Defender for Endpoint? Microsoft Defender for Endpoint is an endpoint security service that offers advanced protection, both proactively and reactively based on a combination of known threats and vulnerabilities, endpoint behavioural analysis and cloud security analytics. Threats can be remediated automatically or manually depending on both the automation level configuration and theContinue reading “Defender for Endpoint”
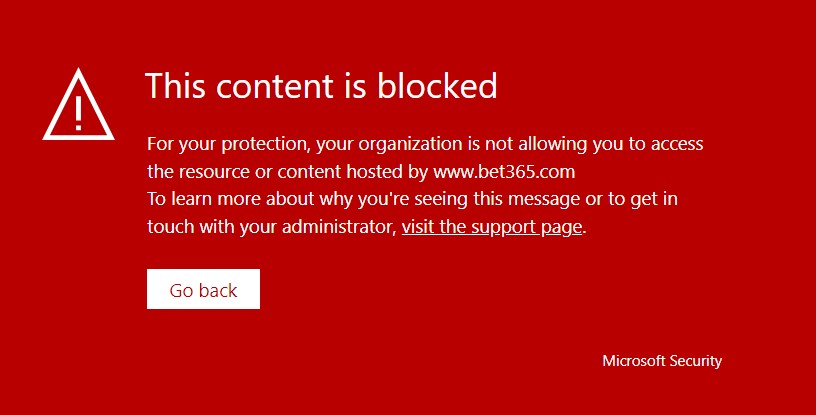
Defender for Endpoint – Web Content Filtering
What is Web Content Filtering? Web Content Filtering provides the ability to manage which web content users have access to and if applicable, block access to specific or pre-categorised content. There are also softer options such as auditing content which is accessed, warning users when potentially inappropriate content is accessed and options to limit theContinue reading “Defender for Endpoint – Web Content Filtering”
BitLocker Startup PIN for Surface (and other tablet) devices via Intune prerequisite
For additional protection, some organisations wish to make use of the additional startup PIN with BitLocker encryption feature which effectively enforces a PIN before presenting the Windows logon screen. As part of the NCSC security guidance for end user Windows desktop OS devices, their recommendations for BitLocker on Windows 10 devices include enabling the startupContinue reading “BitLocker Startup PIN for Surface (and other tablet) devices via Intune prerequisite”
M365 Attack Simulation Training
What is Attack Simulation Training? Attack Simulation Training is a feature within Microsoft 365 that allows you to manage simulations and send them to users within the organisation to validate users awareness and behaviour when receiving what could potentially be harmful content and jeopardise the security posture of the organisation. For example, test phishing emailsContinue reading “M365 Attack Simulation Training”
Obtaining Autopilot Diagnostics
In this post I’ll be detailing how to use the Get-AutopilotDiagnostics PowerShell script to obtain further information on the status of Autopilot during the provisioning process. This will help to troubleshoot failures and identify the potential source of the failure e.g. repeated failure of a particular application install. I havent created this script, all creditContinue reading “Obtaining Autopilot Diagnostics”